In August 2022, Taiwan experienced a significant Distributed Denial of Service (DDoS) attack targeting government digital infrastructure, including the Ministry of National Defense. Using KASPR Datahaus’s global internet monitoring and differential analytics, we were able to identify, isolate, and characterize the event in near real-time.
Unlike traditional network-level monitoring, KASPR measures the entire IPv4 address space, collecting billions of latency and connectivity observations daily. This allows us to differentiate between government, commercial, and residential networks, and to observe how a targeted cyberattack manifests across these different digital layers.
Monitoring the Government IP Space
To focus specifically on the affected entities, KASPR analysts filtered Taiwan’s IP space for endpoints associated with Government organizations in their ISP or ownership records.
Examples include:
By isolating these IP ranges, we could directly monitor active IP counts and average latency responses to detect structural anomalies within government networks.
The DDoS Event
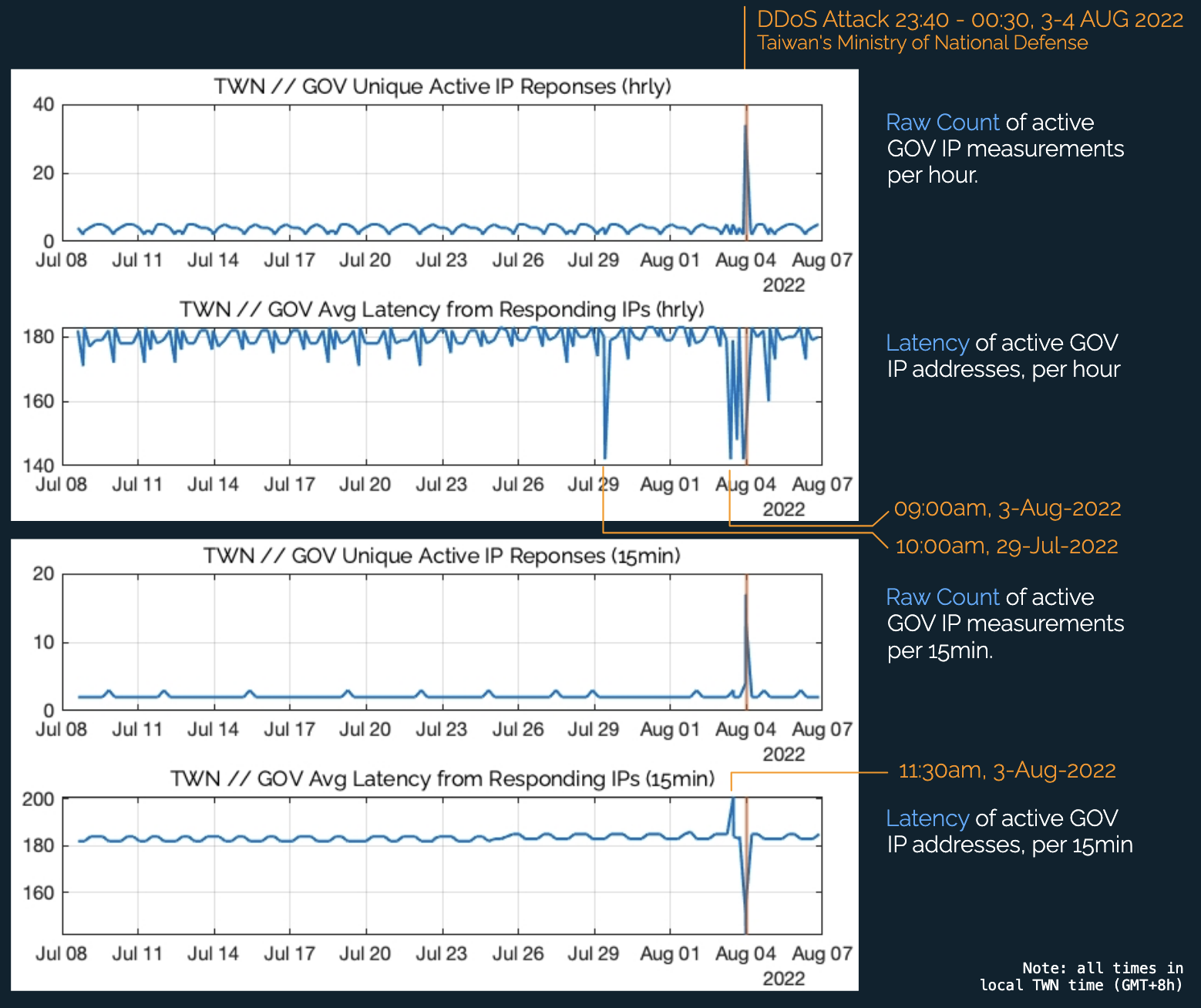
Between 23:40 and 00:30 local time (GMT+8), August 3–4, 2022, a sharp disturbance appeared in Taiwan’s government internet activity.
The two KASPR time series — active IP counts (top panels) and average latency (bottom panels) — clearly reveal the signatures of a DDoS event.
- Spike in Active IP Responses:
Previously unresponsive IPs suddenly began responding. This could indicate either automated countermeasures coming online or attacker traffic overwhelming endpoints, causing false responsiveness signals. - Drop in Average Latency:
Newly active IPs displayed lower latency, or higher-latency IPs were knocked offline — both consistent with large-scale DDoS activity where only a subset of network resources remain reachable. - Temporal Correlation:
These patterns align precisely with the reported window of the Ministry of National Defense’s DDoS incident, confirming that KASPR’s independent, global measurement system captured the event as it unfolded.
The Power of Differential Analysis
Because KASPR monitors all categories of internet infrastructure, we can conduct differential analysis — comparing how different sectors (government, commercial, residential) behave during a network shock.
In this case:
- Government endpoints exhibited severe, short-lived disruptions.
- Residential and commercial networks maintained stable response patterns.
- The divergence confirmed that the anomaly was targeted, not systemic or regional.
This level of discrimination is critical for cyber situational awareness. It allows decision-makers to quickly determine whether a connectivity failure stems from a localized attack, technical failure, or broader network degradation.
Monitoring Recovery
Following the initial attack, KASPR’s data shows a gradual normalization of latency and endpoint responsiveness across government networks.
Within hours, both metrics returned to their pre-event baselines — an indication that Taiwan’s digital infrastructure had effectively mitigated the DDoS load.
Continuous measurement enabled:
- Real-time tracking of remediation progress.
- Verification of service restoration across distinct institutional networks.
- Data-driven reporting on the scale, duration, and intensity of the incident.
Why It Matters
This case highlights the unique value of KASPR’s technology for cybersecurity, defense, and public-sector resilience:
- Comprehensive visibility across entire national internet infrastructures.
- Entity-level differentiation, distinguishing government from civilian networks.
- Early warning capabilities, detecting DDoS and disruption events before they escalate.
- Independent verification, providing third-party transparency and accountability.
By transforming raw global network data into real-time situational awareness, KASPR empowers governments, telecom providers, and security agencies to better understand, prepare for, and respond to digital threats.
KASPR Datahaus — Mapping and protecting the world’s digital infrastructure in real time.